Cloud servers
The CANedge2 can be used with multiple cloud servers for convenience and scalability.
Table of Contents
Amazon [recommended]
- Sign up for a free AWS account and login
- Open this link in a new tab[1]
- Specify a bucket name[2] and click ‘Create stack’ (wait 2 min)
- Go to ‘Outputs’, copy the values into your Configuration File via the editor and save it
- Load the file in the CANcloud login page and verify that you can access the S3 bucket
- Once verified, click the ‘Delete’ button in the AWS stack view to clean up[3]
Example: CANedge2 AWS S3 server configuration
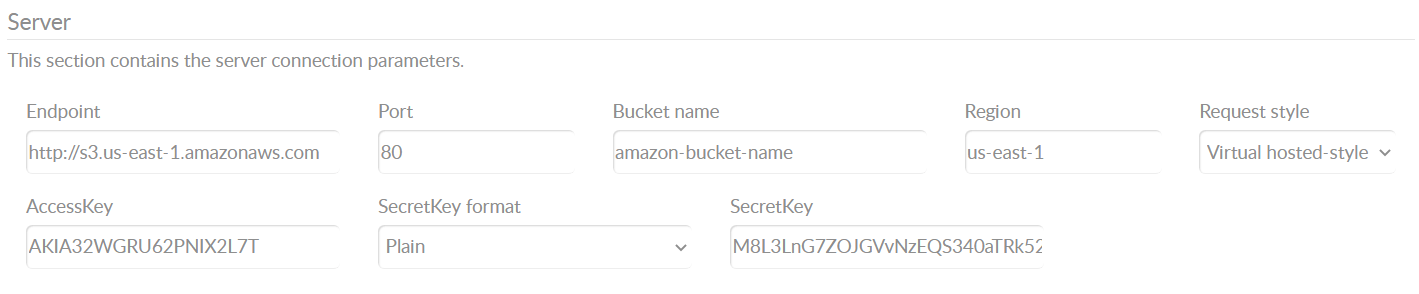
AWS S3 - user policies
The above process creates an IAM user with full S3 access to the created bucket.
For some use cases, you may want to replace this policy - or add separate users. For this purpose, we provide some example policies below (you should replace your-bucket with your bucket name). Make sure to fully test that the new policy works as expected - the below have been tested on FW 01.07.05.
S3-bucket-access: Only allows access to S3 calls for your bucket [DEFAULT]S3-bucket-access-restrictive: As above, but only the S3 calls required by the CANedge2S3-bucket-access-upload-only: As above, but only upload of files (disabling OTA support)S3-bucket-access-read-only: Read-only access for your bucket [not for use on CANedge2]
Google
Google Cloud Storage supports S3 via ‘Interoperability’:
- Sign up for a free account (this requires your card details, but no charges are made)
- Go to ‘Cloud Storage/Create’ and specify a bucket name
- Select a nearby single region (do not use multi/dual regions)
- Go to ‘Settings/Interoperability’ to get your endpoint/keys
- To enable CORS, start Google Cloud Shell via the
>_icon in the upper right corner (video) - Enter the following command:
echo '[{"maxAgeSeconds": 3600, "method": ["GET", "OPTIONS", "HEAD", "PUT", "POST", "DELETE"], "origin": ["*"], "responseHeader": ["*"]}]' > cors-config.json
- Run this in the shell with your bucket name:
gsutil cors set cors-config.json gs://your_bucket - Copy the S3 details into your Configuration File via the editor and save it
- Load the file in the CANcloud login page and verify that you can access the S3 bucket
Example: CANedge2 Google Cloud S3 server configuration
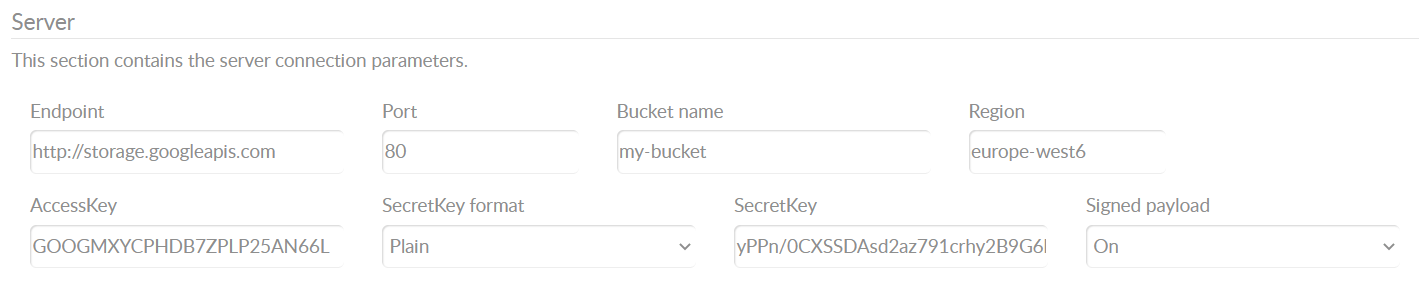
Azure
Azure does not support S3 natively - but you can add a Flexify S3 gateway for your Blob Storage container in 1 min. It is easy, secure and practically free[4].
Below we assume that you already have an Azure Blob Storage container:
- Sign up for a free Flexify account and login (no credit card required)
- Click the ‘…’ next to your Azure Blob Storage container to create a SAS token[5]
- In Flexify, go to ‘Data/Add storage account’, select Azure and add your token and container
- Next, go to ‘Endpoints/New endpoint’ and attach your storage account
- Use the
http://s3.flexify.ioendpoint for initial testing - Copy the S3 details into your Configuration File via the editor and save it
- Load the file in the CANcloud login page and verify that you can access the S3 bucket
Example: CANedge2 Azure-Flexify Cloud S3 server configuration
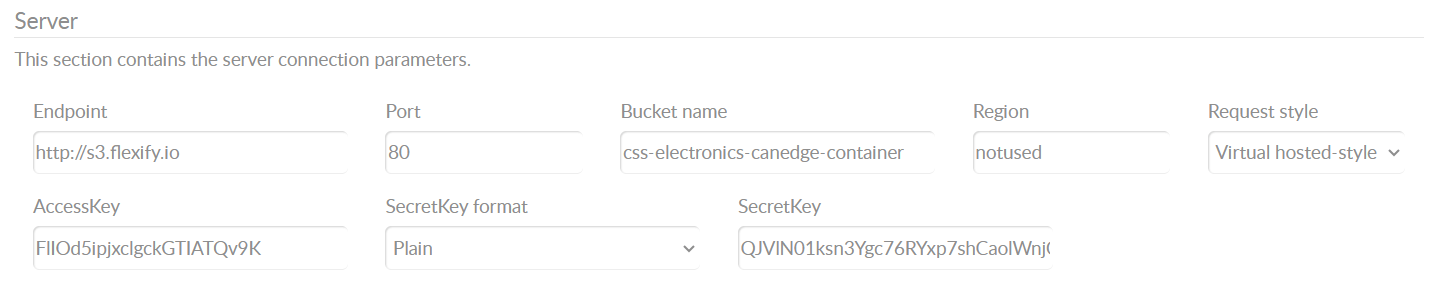
Note
Once you’ve verified the initial connection, select the endpoint with the most nearby region[6]. Note that for the regional Flexify endpoints, you must enable TLS to connect
Other clouds
You can also use other S3 cloud servers like Wasabi or DigitalOcean. The concept of setting these up is similar to e.g. AWS and hence not described in detail here. If questions, please contact us.
| [1] | The link opens an AWS CloudFormation ‘quick-create’ stack. This is a concept that allows for deploying pre-defined resources within your AWS account. The linked template creates an S3 bucket and a new IAM user with full access to the S3 bucket (but nothing else). The template also adds the CORS policy required for you to access the S3 bucket via CANcloud. If you are not the AWS account owner, you can forward the guide to the relevant persons. If you prefer a more ‘manual’ setup, see our original step-by-step guide. For regions in China, use this URL to create your S3 bucket. |
| [2] | The bucket will be created in the region that is currently active in your AWS console, which will generally be recommended if your deployment is near your own location. You can optionally change the region by changing this in the AWS console upper right corner. Selecting a region near your device deployment is key to ensuring fast data transfer rates. |
| [3] | Deleting the stack removes the sensitive details from the Outputs tab and ensures that the created resources are controlled independently of the stack. Your resources are not deleted (i.e. your S3 bucket, IAM user and credentials). We recommend double checking that you can still log in to your S3 bucket after the stack is deleted. |
| [4] | Flexify charges an insignificant 0.04$/GB uploaded/downloaded (zero fixed fees). Your account will start with 20$ free credits (~500 GB data) without the need for adding a credit card up front. You can add more credits as you progress. |
| [5] | Enable all access rights and ensure the token has a sufficient life time for your project |
| [6] | If you are e.g. in EU and only have US based Flexify endpoints available, consider creating an Azure Blob Storage container in a US region as well to minimize the total latency for the CANedge |